Summary
The Automated Certificate Management Environment protocol (ACME) is a protocol for automating certificate lifecycle management communications between Certificate Authorities (CAs) and a company’s web servers, email systems, user devices, and any other place Public Key Infrastructure certificates (PKI) are used. The ACME protocol has no licensing fees, and it requires very little time for IT teams to configure and execute their certificate management automation, making it an increasingly adopted component of enterprise security.
How Does the ACME Protocol Work?
The two communication entities in ACME are the ACME client and the ACME server. The ACME client uses the protocol to request certificate management actions like issuance or revocation. The client runs on the user’s server or device that needs to be protected by the PKI certificate. The ACME server runs at a Certificate Authority, like Sectigo. It responds to the client requests and executes the requested actions once the client is authorized. The communication between the two is based on JSON messages over a secure HTTPS connection.
Sectigo
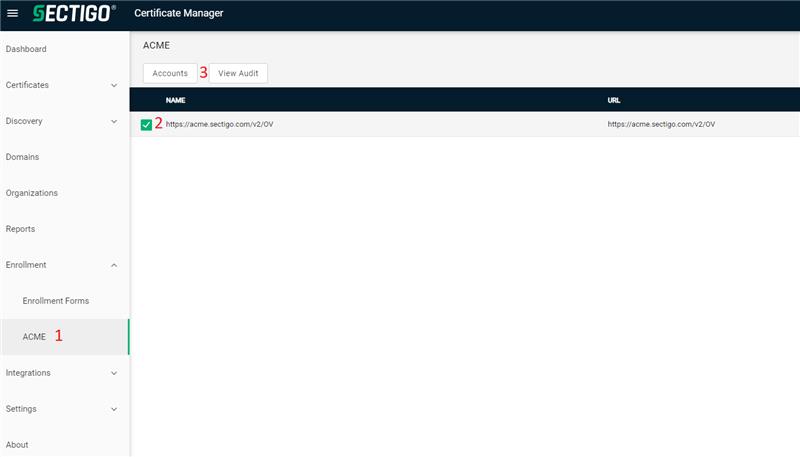
To get started, first login to Sectigo certificate manager, on the left side under enrollment you will find the ACME tab (1). Next click on https://acme.sectigo.com/v2/OV (2) and then Account (3) to create a new ACME account.
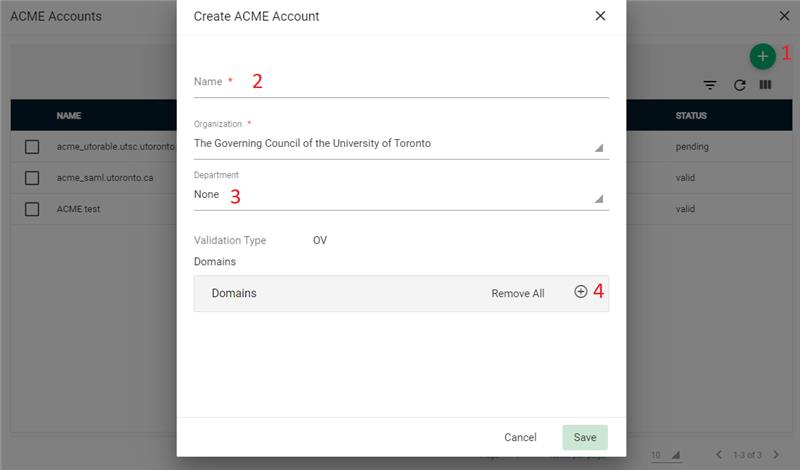
Next you need to create a new ACME account by pressing the green button (1), which will pop up the new “Create ACME Account” Window. You will need to give your ACME account a name (2), it is recommended to create a new ACME account for each domain and use the domain name for your ACME account name. Department (3) will have your department already filled out if you are in a department or None if you don’t have a department or are in multiple. Please selected the corresponding department base on the Domain. Next you will need to add the Domain by press the add button (4). You can find the Domain from a drop-down menu, if you don’t see the Domain please check if you selected the correct Department and if the domain doesn’t yet exist you will need to add the Domain.
When the account is created Sectigo will generate the Keys needed to connect an ACME client to the ACME server. You can find the page again by selecting your ACME account and clicking Details.
ACME client
After creating and setting up an ACME account on Sectigo and receiving the keys. User first decides which client to use and then installs the client onto the domain/server to use the ACME protocol. Some popular ACME clients are:
- Certbot by Electronic Frontier Foundation (EFF) and sponsored by Sectigo
- ACMESharp
- acme-client
- GetSSL
- Posh-ACME
Following is an example of how to use CertBot. Go to https://certbot.eff.org/ and install certbot base on your software and system. Next, you can simply follow the example given by Sectigo.
certbot certonly --standalone --non-interactive --agree-tos --email <email> --server https://acme.sectigo.com/v2/OV --eab-kid <kid> --eab-hmac-key <key> --domain <domain> --cert-name <cert-name>
This will generate a new certificate at the path /etc/letsencrypt/live/<cert-name>/fullchain.pem and the key at /etc/letsencrypt/live/<cert-name>/privkey.pem. The above command is standalone so it will not integrate with webserver and will need to install the certificate by changing the config file of your webserver to point to the new path or moving the certificates and private key. If you are using apache, nginx, webroot, you can change –standalone to –apache, –nginx, or –webroot to automatically obtain and install certificates.
ACME will automatically renew certificate; you can check the command to renew is installed in one of the following locations:
- /etc/crontab/
- /etc/cron.*/*
- systemctl list-timers
To see all certificate currently managed by ACME use the “certbot certificates” command
To delete a certificate used the “certbot delete”
API
If you want to use API to generate acme accounts and assign domains to the account
Use the following to create a new acme account
curl 'https://cert-manager.com/api/acme/v2/account' -i -X POST \ -H 'Content-Type: application/json' \ -H 'login: account' \ -H 'password: password!' \ -H 'customerUri: uot' \ -d '{"acmeServer":"https://acme.sectigo.com/v2/OV","name":"apitest","organizationId":6339}'
use this to find the id of the newly create acme account where name=<new acme account name>
curl 'https://cert-manager.com/api/acme/v2/account?position=0&size=10&organizationId=6339&name=apitest&acmeServer=https://acme.sectigo.com/v2/OV&status=Pending' -i -X GET \ -H 'login: account' \ -H 'password: password' \ -H 'customerUri: uoft'
use this to add domains to the newly created acme account “account/<new acme accound id>/domain”
curl 'https://cert-manager.com/api/acme/v2/account/24282/domain' -i -X POST \ -H 'Content-Type: application/json' \ -H 'login: account' \ -H 'password: password' \ -H 'customerUri: uot' \ -d '{"domains":[{"name":"si.utoronto.ca"}]}'