Click here to see a list of the applications and vendors that have been assessed by ISEA or others that ISEA knows about.
The diagram below captures the steps involved in a project Information Risk Management Assessment. It is derived from a diagram in ISO27005, with a modification added from NIST SP 800-39, and further modified to apply to the requirements of UofT.
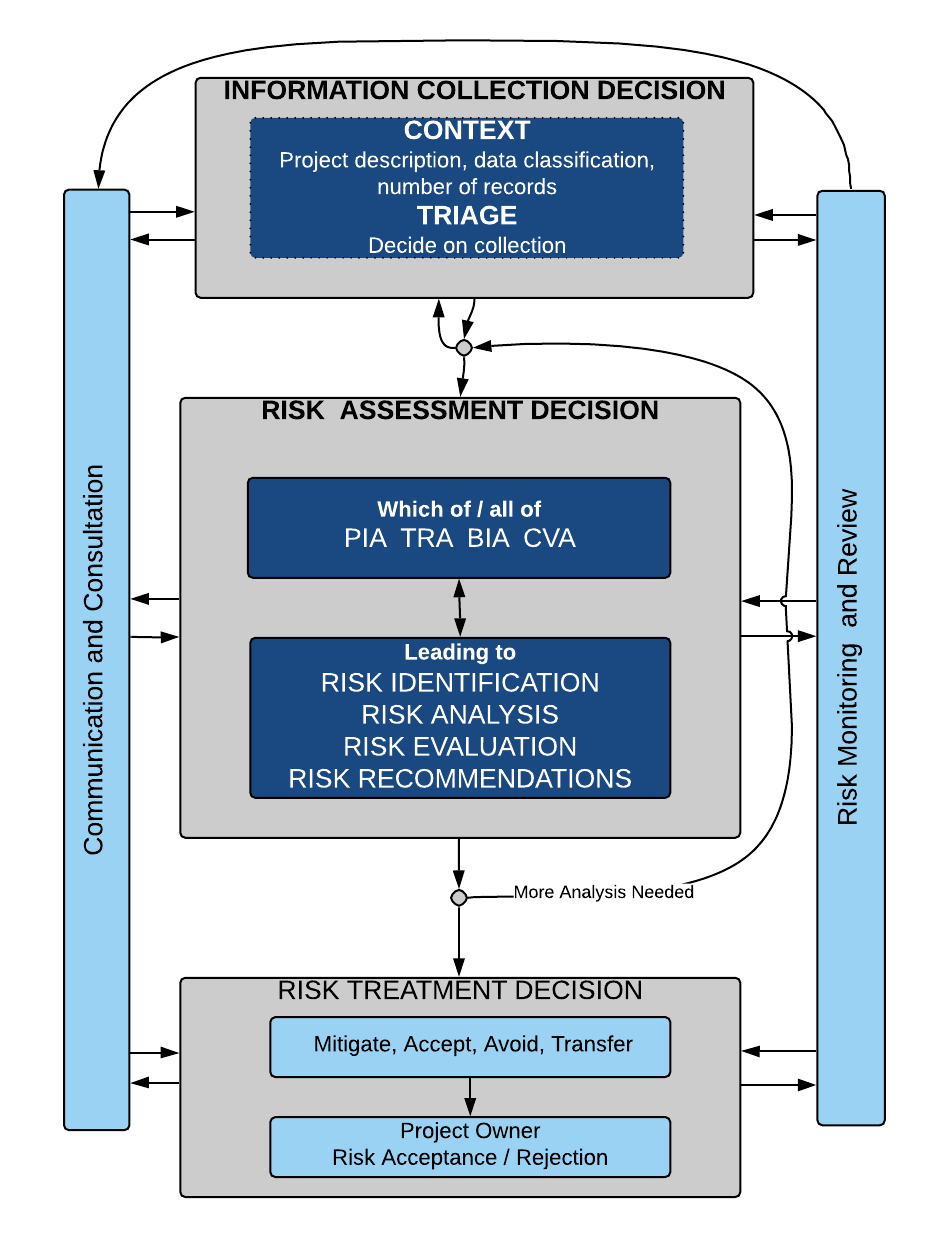
The depth of risk assessment depends on the information used in the project and the quantity.
Step 1. Determine the context – provided by project owner.
What is the project, what type of information will be collected or used?
Step 2. Decide on the depth of detail about the project / vendor that needs to be collected – in discussion with ISEA
- If the information is public, then possibly a light risk assessment needs to be completed, and the detail needed is small.
- If the information is level 3 or 4, or there are a large number of records:
- ISEA provides an UofT-Information-Risk-Management-Questionnaire (IRMQ) to capture the detail; or
- The HECVAT may be used by vendors
- this reduces duplication of effort for vendors in the higher education space. Some already have a HECVAT completed and available on request
- The HECVAT does not capture all necessary details relating to use of personal information.Vendors must also complete parts of the IRMQ, particularly pertaining to personal information, and third parties. Sections required are clearly explained in the IRMQ.
Step 3. Risk Assessment
The detail collected about the project / vendor are analyzed. Depending on the project one or all of a Privacy Impact Assessment (PIA), a Threat/Risk Assessment (TRA) and a Cloud Vendor Assessment (CVA) will be carried out – together called the Information Risk and Risk Management Assessment (IRRM)
- ISEA will complete an IRRM of your project or process, possibly at a fee, depending on the assessment; or
- ISEA will provide help for you to complete your own assessment; or of course
- You are free to carry out your own assessment. If you want to make use of it, ISEA provides an Information Risk Management Assessment template.
Managing the risk
- After analysis, the project team need to respond to the recommendations to manage risk, by mitigating the risk (making changes), accepting, transferring or avoiding the risk.
Continuous risk monitoring
- On a continuing basis, the project needs to be monitored for risk, and reviewed at intervals to ensure the goals of the risk management assessment are being met. This is an iterative process, as threats constantly evolve, and new vulnerabilities are discovered.
Communication
- The steps require communication and consultation between stakeholders.
What is the HECVAT?
- Educause provide a Higher Education Cloud Vendor Assessment Tool (HECVAT), in two version, Full and Light. This is useful, as vendors then provide only one set of answers for all institutions. Please see https://www.ren-isac.net/public-resources/hecvat.html.
- In general, the full version would be used, unless there is no or very little personal information.

