Background
The University’s certificate authority service run by Sectigo has produced many certificates that are signed by the “USERTrust RSA Certification Authority” and “AddTrust External CA Root”. Your chain may expire, prematurely, on May 30th. This document is a guide to determining if you server’s chain has a problem.
As of April 30th, 2020, the certificate chains are signed with “AAA Certificate Services” global root certificate. These certificate will not expire on May 30th and so they need no fixing.
How to Determine if Your Certificate Chain is Expiring
Unfortunately, that’s not always simple, though it is for public web sites. If your service is a web site and it’s not firewalled, then SSLlabs.com offers an SSL evaluation that you can use. If your service is not public or not a web server, it’s a little more difficult.
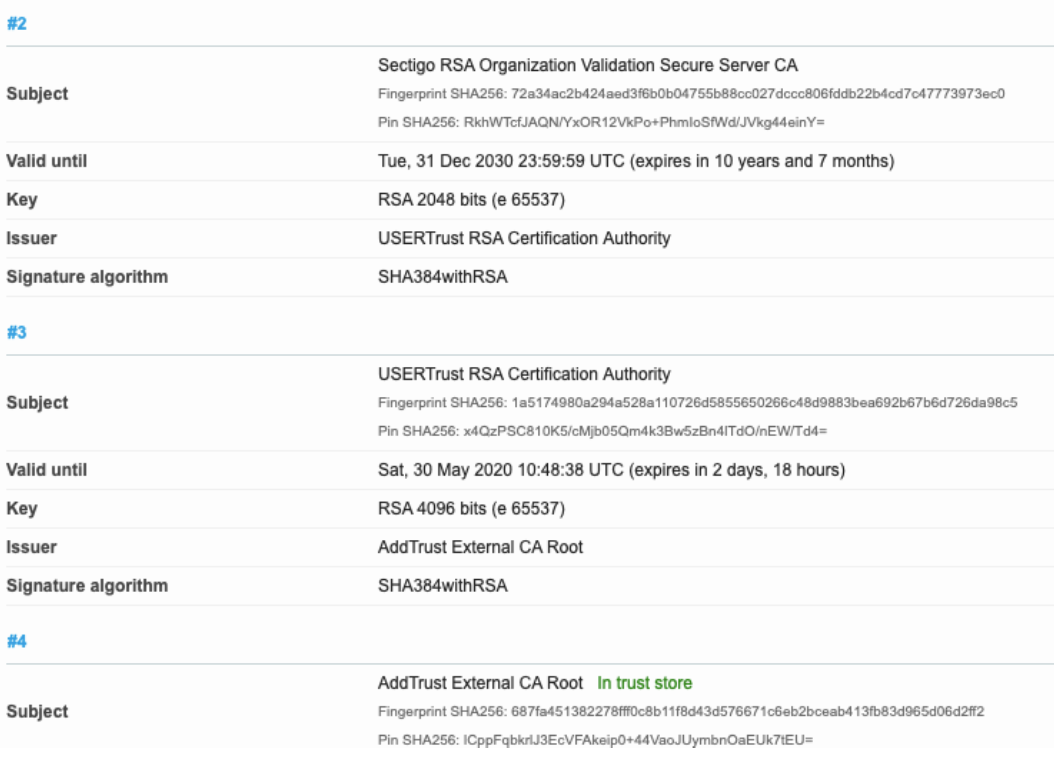
If your certificate is for a public web server. You can visit SSL labs: https://www.ssllabs.com/ssltest/index.html
Enter your site’s domain name and SSL labs will evaluate it and produce a report. It takes a minute or so to fetch and evaluate your server and its certificate chain. After the “Summary” section, is a “Certificate #1: …” report with an “Additional Certificates (if supplied)”” subsection. In this subsection, you’ll find “#2’, “#3”, with report of the “Valid until” date. You’ll have a problem if any of these certificates is expiring soon: i.e. before your Certificate #1 expires. For our soon-to-expire Sectigo certificate chain, you’ll see: